Hello friends!
Today i will teach you how to hack a pc with metasploit
Note: This is an advance topic.Read Carefully. Feel free to ask any kind of queries . We are always here to help you.
If you are really interested in network security, chances are you must have heard of the Metasploit over the last few years.
Now, have you ever wondered what someone can do to your PC, by just
knowing your IP. Here’s the answer. He could 0wN you, or in other words ,
he could have full access to your PC provided you have just a few
security loopholes which may arise cause of even a simple reason like
not updating your Flash player last week, when it prompted you to do so.
Metasploit is a hacker’s best friend, mainly cause it makes the job of
exploitation and post-exploitation a lot easier compared to other
traditional methods of hacking.
The topic Metasploit is very vast in itself. However, i’ll try keeping
it basic and simple so that it could be understood by everyone here.
Also, Metasploit can be used with several other tools such as NMap or
Nessus (all these tools are present in Backtrack ).
In this tutorial, i’ll be teaching you how to exploit a system using a
meterpreter payload and start a keylogger on the victim’s machine.
Hacking through Metasploit is done in 3 simple steps:
Point, Click, 0wn.
Before I go into the details of The Metasploit Framework, let me give
you a little idea of some basic terms (may seem boring at first, but
you must be knowing them)






.jpg)



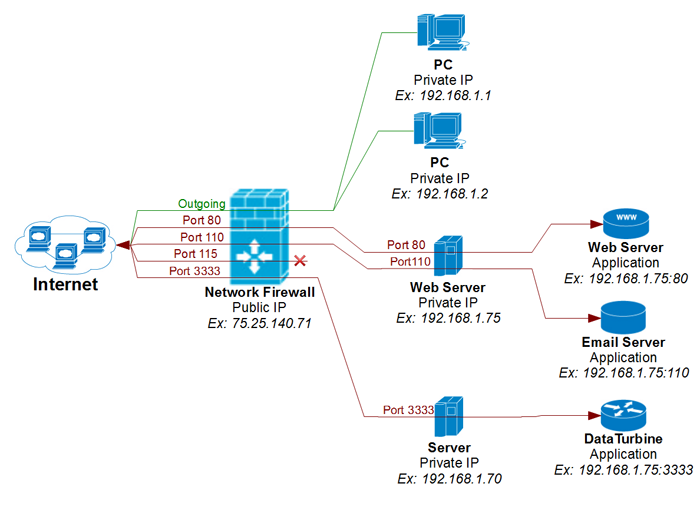 In the previous tutorial, we created a
In the previous tutorial, we created a 

